Threat Detection
Empowering your business with strategic insights, seamless integration and latest technology.
Transformative Solutions
Strategic Partnership
We believe in building long-term relationships not just delivering projects. We work closely with your team to understand your challenges and objectives, ensuring every solution we deliver adds strategic value and supports sustainable growth.
Tech Integration
Our strength lies in seamlessly integrating new technologies into your existing ecosystem. Whether it's cloud migration, AI integration, or DevOps adoption, we ensure smooth transitions that enhance functionality without disrupting operations.
Business Growth
We don't just provide tools we empower your team to leverage them effectively. Through intuitive interfaces, automated workflows, intelligent insights, and ongoing support, we help you maximize ROI and stay agile in a constantly evolving digital landscape.
Cyber Defense
Proactive protection for your systems, data and people in a constantly evolving threat landscape
Shielding Your Business Against Evolving Cyber Threats
In today’s hyper-connected world, cyber threats are more sophisticated, targeted, and relentless than ever. At Proxenic, our Threat Protection services are designed to safeguard your digital infrastructure, users, and critical data with advanced, proactive security solutions that detect, prevent, and neutralize attacks in real time.
- Continuously monitor your infrastructure to detect unusual patterns and potential intrusions instantly.
- Utilize behavior analysis and machine learning to spot and stop hidden threats before they spread.
- Block malicious emails, fake websites and impersonation attempts with robust phishing protection tools.
Why Threat Protection Matters
Modern businesses rely on interconnected systems that expose them to risks like malware, ransomware, phishing, insider threats, and advanced persistent attacks. A security breach doesn’t just cause downtime it damages reputation, disrupts operations, and leads to significant financial loss.
- Protect all connected devices across your network with centralized, automated endpoint defense.
- Stay ahead with up-to-date threat intelligence feeds and predictive security analytics.
- Receive expert support and fast action plans when incidents occur minimizing impact and recovery time.
Our Numbers Speak
Multi-Cloud Strategy
Leverage the power of AWS, Azure and Google Cloud to balance cost, performance and resilience.
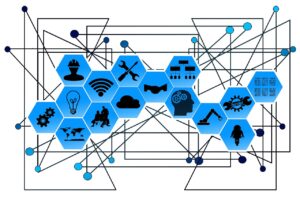



Compliance Excellence
Our Approach to Threat Protection
We combine real-time threat intelligence, AI-driven detection tools and layered defense models to ensure your business stays resilient in the face of cyber threats. Our services are tailored to your environment whether cloud-based, hybrid or on-premise. With automated alerts and continuous security assessments, we empower your organization to defend against threats before they become breaches ensuring business continuity and regulatory peace of mind.
Smart, secure and scalable solutions tailored for your transformation journey.
Digital Excellence
Complete Expertise
From initial consultation to post-deployment support, we offer comprehensive services that cover every stage of your digital transformation journey. Our diverse expertise ensures seamless integration, security and performance across all layers of your IT ecosystem.
Scalable Security
Our solutions are engineered for scalability and security without compromising on innovation or performance. Whether it’s multi-cloud architecture, intelligent automation, or advanced threat defense, we help your business grow with confidence, control, and clarity.
Innovative Solutions
We don't just follow trends we build future-ready technologies that solve real business problems effectively and sustainably. Our client-centric approach ensures that every solution is practical, measurable, scalable and aligned with your strategic goals and long-term vision.
We work with businesses across various sectors including finance, healthcare, retail, logistics and tech. Our scalable solutions are designed to adapt to industry-specific challenges and compliance requirements.
We design systems using modular architectures and cloud-native technologies that grow with your business. Whether you’re scaling up operations or expanding globally, our solutions evolve to meet your demands.
Absolutely. We provide continuous post-deployment support, including performance monitoring, updates, security checks and technical assistance to ensure your systems remain secure and efficient.
We implement end-to-end encryption, threat detection, access controls and compliance frameworks like GDPR, HIPAA, and ISO standards to ensure your data stays safe and compliant.
Yes. We specialize in seamless integration with legacy systems, cloud platforms, third-party APIs and custom applications minimizing disruptions and maximizing compatibility.
Our innovation-first mindset, deep technical expertise, and client-centric approach set us apart. We don’t just deliver solutions—we build strategic partnerships focused on your long-term success.